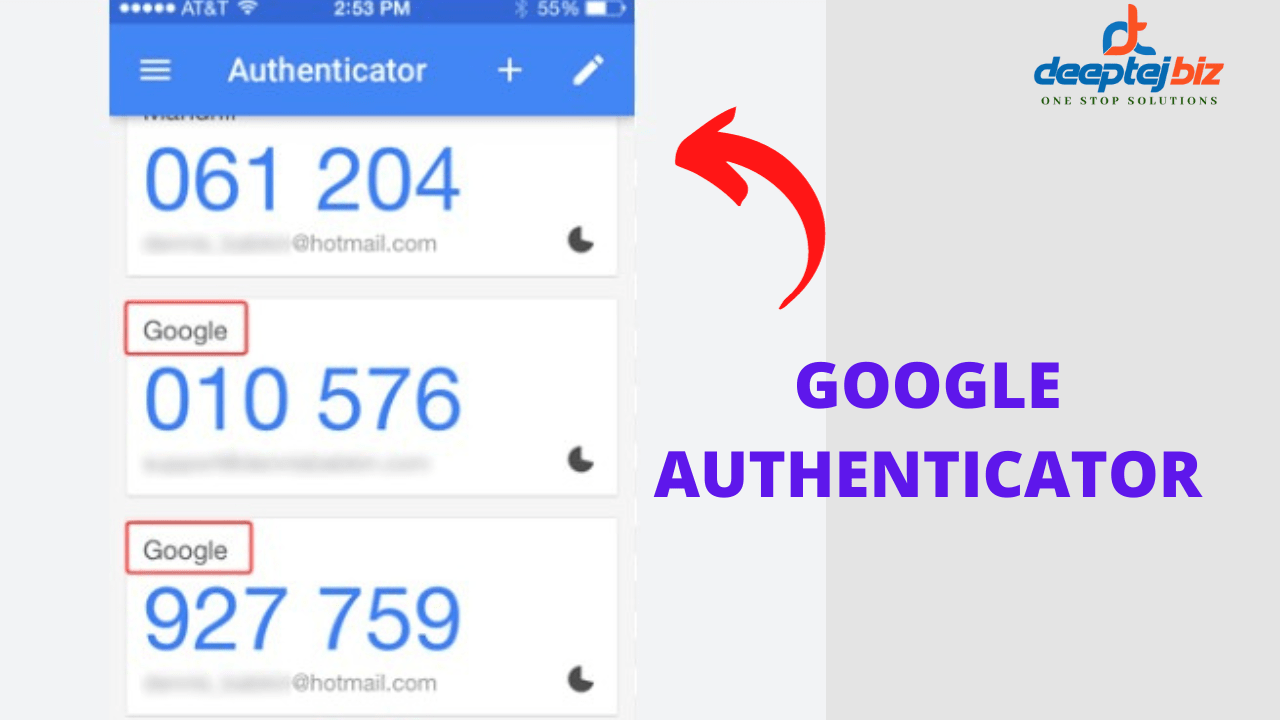
Online Educational Fraud and Personal Loan Scams
How to Prevent from Online Educational Fraud and Personal Loan Scams Online Educational Fraud, often promising to provide educational qualifications in just a single day, has become a concerning trend. This article is your guide to understanding the risks associated with such fraudulent schemes and how to safeguard yourself against financial educational loans that claim to expedite your education in the blink of an eye. The Growing Threat of Online Educational Fraud Online Educational Fraud involves the deceptive acquisition of educational credentials, often through illegitimate online sources. These fraudulent qualifications are then used to mislead employers or educational institutions. In a troubling twist, some individuals are using personal loans to finance their fraudulent educational pursuits. The Consequences of Educational Fraud Financial Loss Victims of Online Educational Fraud may end up…